Integrating Microsoft Active Directory as a Login Provider
Microsoft Active Directory (AD) plays a critical role in enterprise environments, serving as the backbone of identity management for over 90% of Fortune 500 companies. Active Directory is a directory service for managing users, devices, and access permissions, ensuring that employees have the appropriate credentials to access network resources securely. Its widespread adoption stems from its integration with Microsoft services and applications, making it a standard for enterprises running Windows-based systems. It is only natural that Identity must offer seamless native integration with Microsoft Active Directory.
Active Directory Deployment Scenarios
When an enterprise refers to Active Directory, it's essential to probe further to understand the specific components and their deployment architecture. We have come across these 3 scenarios when working with large enterprises.
- Active Directory (On Premise) - Active Directory is an on-premises solution that handles directory services, user authentication, and access management, primarily for Windows-based environments.
- Active Directory with Active Directory Federation Services (Hybrid) - As organizations increasingly adopted cloud technologies, ADFS was introduced to extend AD’s capabilities by enabling Single Sign-On (SSO) and federated identity management, allowing users to authenticate across external systems without storing credentials externally.
- Entra ID, formerly Azure Active Directory (Cloud) - Azure Active Directory, now rebranded as Entra ID, emerged as a cloud-based identity solution, addressing the needs of organizations with hybrid or fully cloud environments.
Introduction
In this post, we will only focus on guiding you through the integration of a traditional Active Directory for Single Sign-On using Identity, our comprehensive Identity and Access Management (IAM) solution that supports OAuth2, SCIM, SAML, and OpenID Connect protocols.
Active Directory Federation Services and Entra ID were built with the intent of Single Sign On and support OpenID Connect. It is straight forward to integrate any solution that supports OpenID Connect, we can create a new Identity Provider and select the protocol as OpenID Connect.
The integration of Active Directory, in this case, does not offer true Single Sign-On. It does not automatically log users in an application if they have already signed in with the same credentials elsewhere (Though this can be achieved through Windows Authentication on supported Web Servers). This is why, we call it a Login Provider. A login provider in Identity is limited to accept user credentials and verify if the credentials are correct.
What You'll Need:
- Access to the Identity server.
- Active Directory details like Server, Port, Bind Credentials, Search Container
- Administrator privileges on Identity.
Step 1: Configure Active Directory as a Login Provider in Identity
We will use LDAP as the protocol to connect to a Microsoft Active Directory. LDAP (Lightweight Directory Access Protocol) is a protocol used for accessing and managing directory services over a network. It allows applications to query and modify directory information, such as user credentials and organizational structures, in a standardized and efficient manner. By using LDAP, you can follow similar steps to connect to other Directory Servers like Apache Directory Server, IBM Security Directory Server, Novell eDirectory or Red Hat Directory Server.
Follow these steps to configure Active Directory as a Login Provider
- Log into Identity Admin Console:
- Access the Identity management dashboard.
- Navigate to the Login Providers Section:
- Administration > Providers > Login Providers
- Click on New Provider
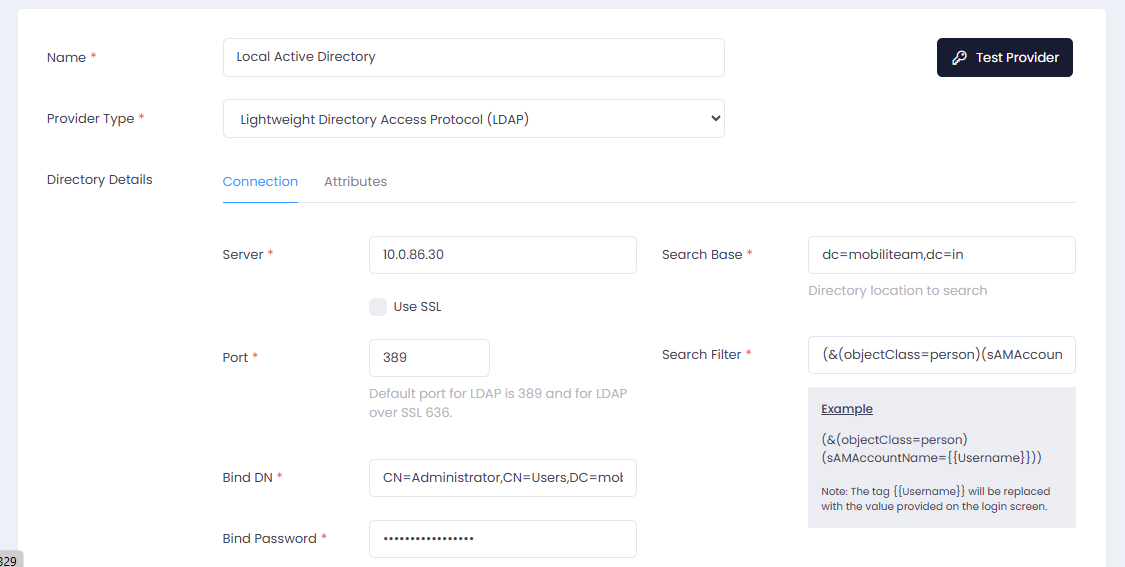
- Enter Active Directory details.
- Server
- Port and SSL
- Bind DN (AD account that has access to perform user search queries)
- Bind Password
- Search Base (Directory container in which a user search is performed)
- Search Filter
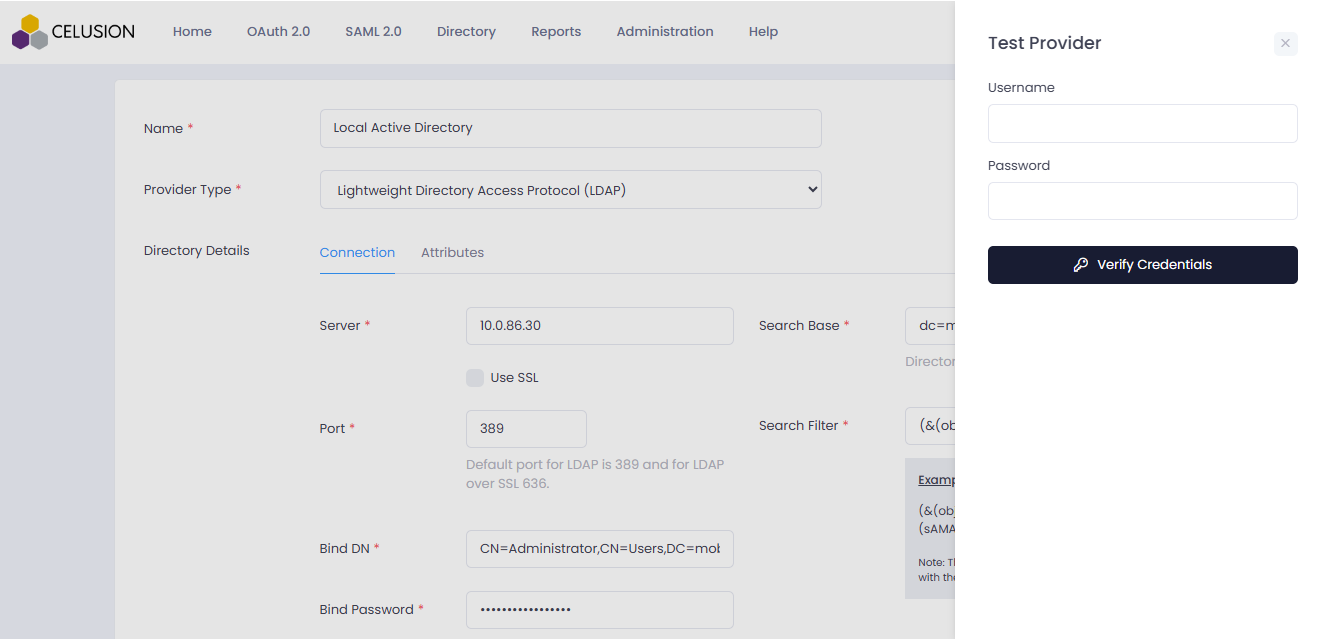
- Test the Provider
- Enter user credentials
- Click Verify Credentials to test your settings
Step 2: Associate the Login Provider to a User
Next we need to create or modify an existing user and configure the user to use Active Directory as the Login Provider
- Navigate to People
- Navigate to Directory > People
- Set the Login Provider
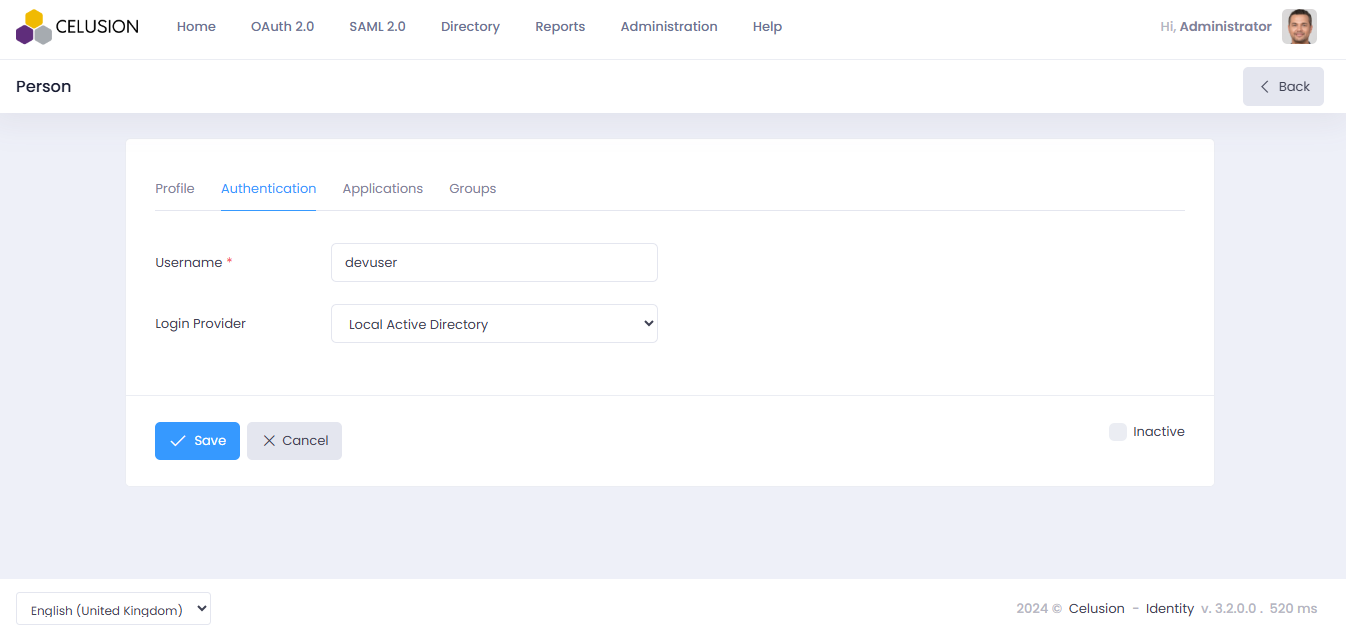
- Create a new user or Select an existing user
- Under the authentication tab, ensure the username is the AD username
- Choose the Active Directory setup in Step 1 as the Login Provider
- Save the user configuration
- Click on Save
Step 3: Testing the Integration
Login to Identity using Active Directory credentials
- Open Identity
- Navigate to Identity Login page
- Enter Active Directory Credentials
- Enter Active Directory username
- Enter Active Directory password
- Login to Identity
- Click Login and you will be navigated to the Identity Home Page.
Under the hoods, Identity verifies the credentials against Active Directory, using the Lightweight Directory Access Protocol (LDAP) and grants user access.
Video Tutorial
We've also created a comprehensive video tutorial on YouTube that walks you through the entire SSO setup process with Active Directory as the Login Provider. Watch it here to see each step in action!
Conclusion
Integrating Active Directory with Identity offers enterprises a robust, scalable, and secure way to manage user access and authentication across both on-premise and cloud environments. Whether dealing with traditional Active Directory, ADFS for hybrid setups, or Microsoft Entra ID for cloud-based solutions, each scenario provides unique benefits tailored to modern organizational needs. By ensuring seamless integration with Identity, enterprises can enhance their identity management processes, streamline authentication, and maintain strong security protocols across applications. This integration is crucial for organizations looking to unify their infrastructure while supporting diverse access requirements and maintaining compliance.





